The article Comparison and Differences Between IPS vs IDS vs Firewall vs WAF briefly introduces the differences between IPS, IDS, WAF, and the firewall. But there are many details that are not included. Especially the difference between firewall and IPS/IDS. In this article, we will introduce in more depth the difference between IPS and firewall as a security defense product.
Firewall
The current mainstream fire protection uses the state detection function to check the legitimacy of the link state of the message, and discard the message with the illegal link state. The core basis is the session state. When user traffic that meets the access conditions traverses the firewall for the first time, a session entry will be generated, and subsequent packets of the session will be forwarded based on this session entry.
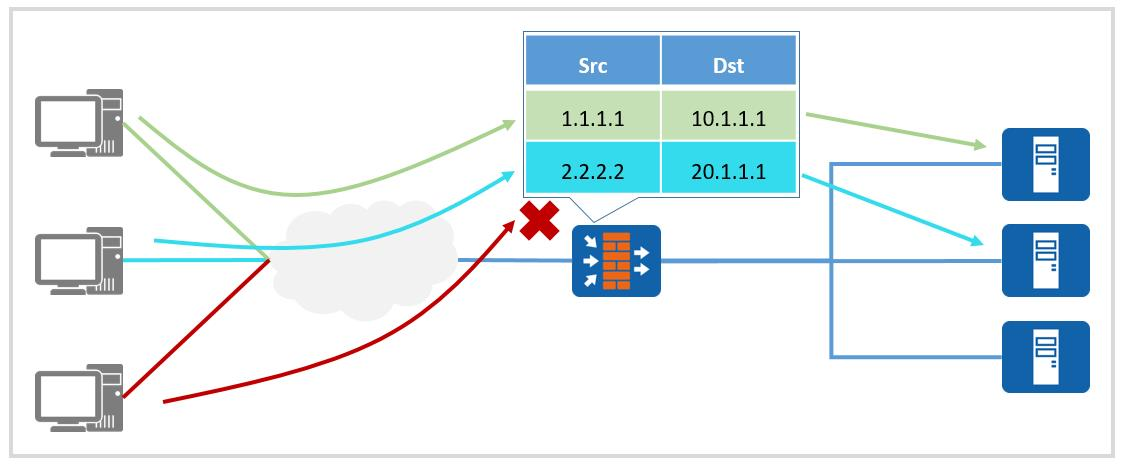
Figure 1: Firewall inspects the traffic based on the pre-configured security policy
Static security defense technology in the firewall: The firewall's judgment on whether the traffic is illegal is often based on the security policy pre-configured by the administrator, which cannot intercept some special attacks. For example, traditional firewalls cannot intercept XSS attacks and SQL injection attacks against web servers.
IPS/IDS
To put it simply, IPS is an advanced version of IDS, which can not only detect threats like IDS, but also block intrusion traffic in real-time, thereby preventing greater losses in time.
Compared with passive detection firewalls, the biggest difference of IPS is its active detection.
Intrusion detection technology enables the security system to respond in real-time to the time and process of intrusion by studying the process and characteristics of intrusion behavior. The technologies used by IPS can be divided into:
1. Anomaly detection: The assumption of anomaly detection is that the activities of the intruder are abnormal from the activities of the normal subject, and an "activity profile" of normal activities is established. When the current subject's activity violates its statistical law, it is considered to be an "intrusion" behavior.
2. Feature detection: Feature detection assumes that the activity of the intruder can be represented by a pattern, and the goal of the system is to detect whether the activity of the subject conforms to these patterns. Feature detection requires signature library support.
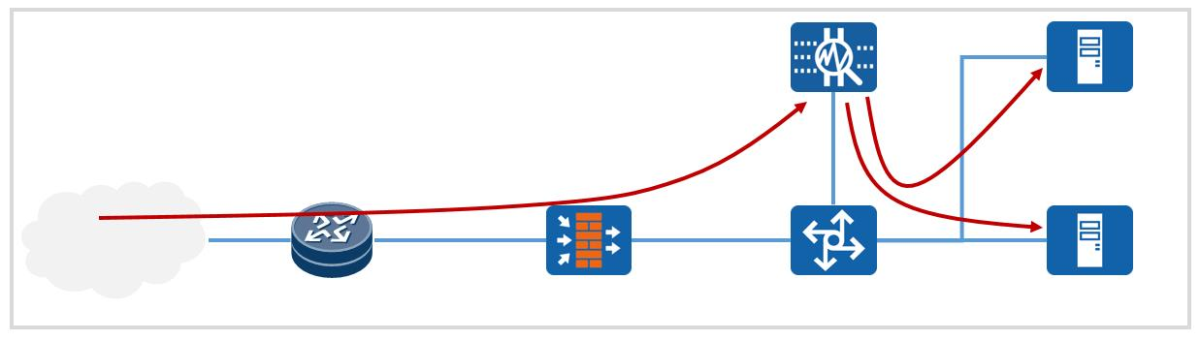
Figure 2: One of the IPS implement location
Usually, IPS adopts the feature detection mode. At this time, the IPS will perform feature inspection on all traffic and block the traffic that meets the intrusion characteristics. Since the signature database can be updated in real-time from the official website of the equipment supplier, IPS can often detect intrusions in a more timely manner.
In addition, as a border device, the firewall distinguishes different areas by zone but does not detect traffic in the same area. This leaves nothing for the attacks launched within the intranet. However, IPS is often deployed at key nodes through which all traffic flows. In addition to detecting external attacks, IPS can also respond to internal attacks.
Why can the firewall also perform content security detection?
For some scenarios where the business volume is not large, deploying IPS and firewalls separately will bring huge hardware cost pressures to the company. In order to alleviate this situation, many manufacturers have introduced firewalls that integrate content security detection, such as Huawei's USG firewall. Based on the security detection and processing capabilities of traditional NGFW firewalls, these devices also support the security analyzer HiSec Insight ( Also known as CIS), FireHunter sandbox, security controller SecoManager and other network security devices are linked, using intelligent detection technology to effectively detect and proactively defend against advanced threats. However, compared to separate IPS devices, these integrated firewalls tend to be slightly inferior in processing performance.
In conclusion
Table 1: The difference between Firewall and IPS
Firewall | IPS | |
Basis for inspection | Pre-configured security policy | Signature |
Deployment location | Network boundary | Intranet backbone node |
Timeliness | Security policy updates rely on administrators | Fast update of signature database |
Detection flow | Cross-region traffic | All traffic |
Performance requirements | Need high hardware | Need high-performance hardware to support real-time detection and forwarding |
Advantage | Other functions can be integrated, cost-effective | Active detection, strong detection ability |
No comments:
Post a Comment